Installing & Configuring Snort (IDS/IPS)
Alex Nelsen
1/29/2024
In this blog post, I will be installing Snort 3.1.78.0 (an Open Source IDS/IPS) onto an Ubuntu Virtual Machine, configuring rules using Pulled Pork & creating alerts for detection of "ICMP Ping" traffic inbound to the VM. I will also be performing a reading of a malicious PCAP file using REGEX and generating a basic signature.
Step 1. Went to Snort.org, created an account, and downloaded the free community ruleset. Account is needed for Oinkcode. (Explained later)
Step 2. Logged into Ubuntu Desktop Virtual Machine on my repurposed Dell XPS with VMWare (Previous blog post). Started with an update & upgrade. "sudo apt-get update && sudo apt-get upgrade -y"
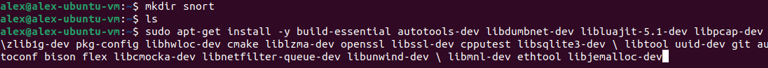
Step 3. Downloaded Snort via Ubuntu. Created directory named "snort". Downloaded Snort prerequisites using the following commands:
Step 4. Once the essentials have been installed, pattern matching requirements for Hyperscan needed to be installed. Snort utilizes Hyperscan for fast pattern matching using REGEX - these consisted of 4 different prerequisites: pcre, gperftools, Ragel, Boost C++ libraries.
pcre:
gperftools:
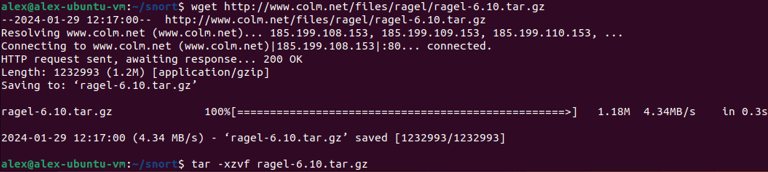
Ragel:
Boost C++ Libraries: (downloaded but not installed)
Step 5. Installed Hyperscan itself & installed additional prerequisites to allow Snort3 to get up and running
Hyperscan:
flatbuffers:
Data Aquisition (DAQ):
Step 6. Updated shared libraries.
Step 7. Downloaded latest version of Snort3 (3.1.78.0)
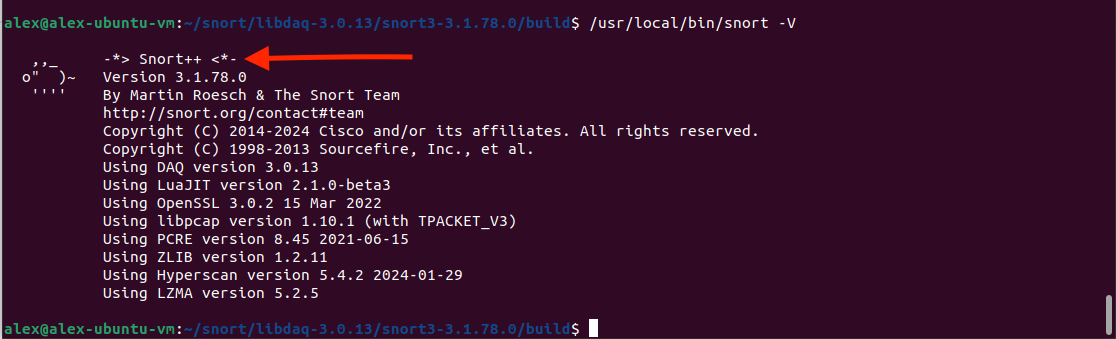
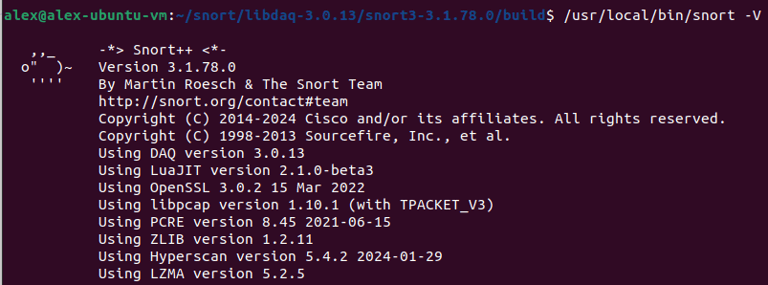
Step 8. Testing Snort:
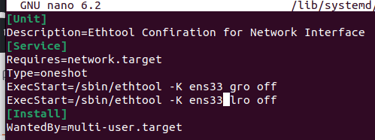
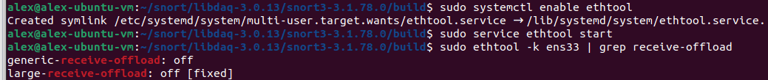
Step 9. Turning off Generic & Large receive offloads (GRO/LRO) on network card using a service. Finding network adapter name using "ip a" - ens33.
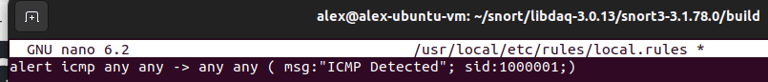
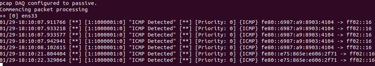
Step 10. Creating a custom rule for Snort to detect & alert to ICMP Traffic (Ping).
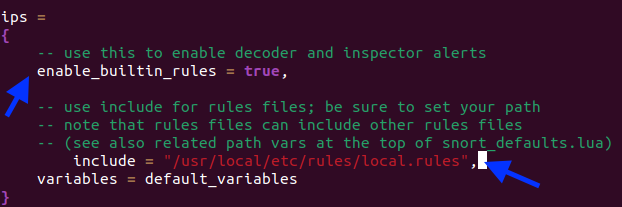
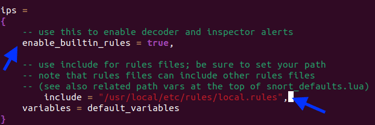
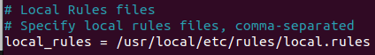
Step 11. Modifying Snort configuration so user (me) does not have to specify the rule locations when running Snort. Edited with "sudo nano /usr/local/etc/snort/snort.lua"
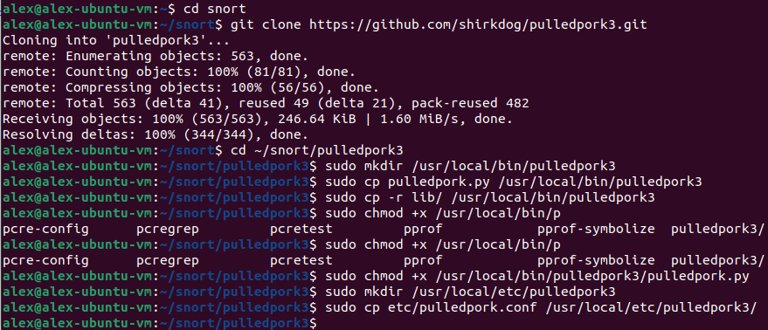
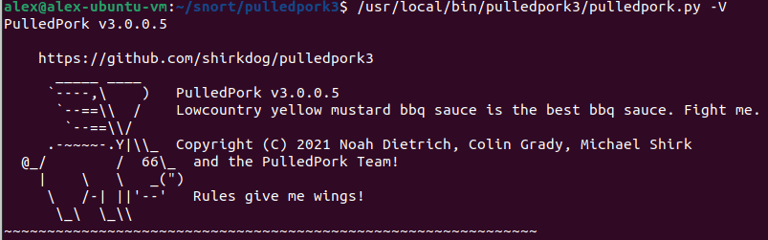
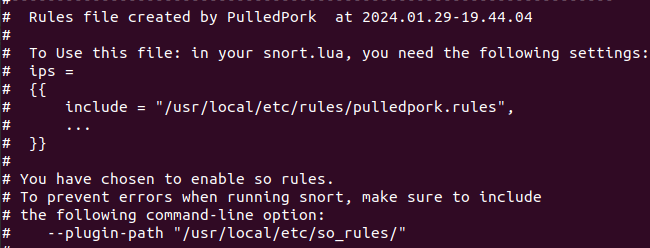
Step 12. Expanding Snort Rule Set. Accomplished by installing "Pulled Pork" which automatically grabs rules - verifying Pulled Pork is running.
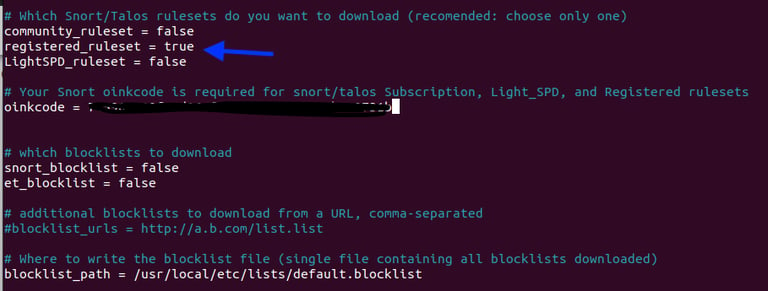
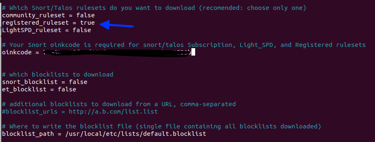
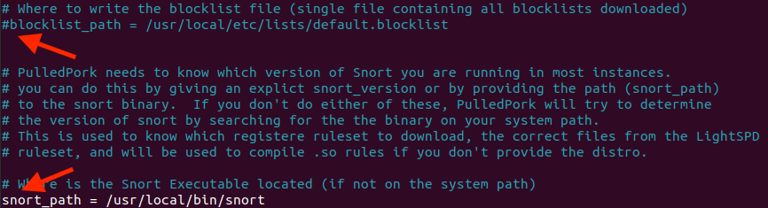
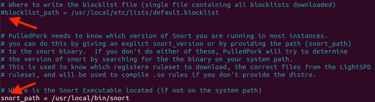
Step 13. Modifying Pulled Pork .conf files - Set registered_ruleset = true, entered Oinkcode, commented out blocklist_path, and enabled both local_rules & snort_path
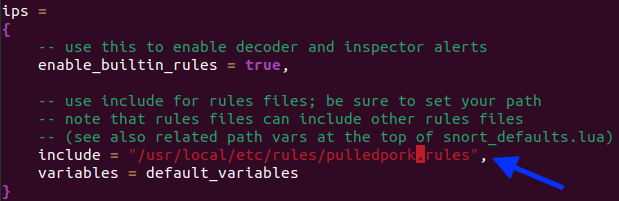
Step 14. Remodifying Snort's .conf file to point to Pulled Pork's Rules.
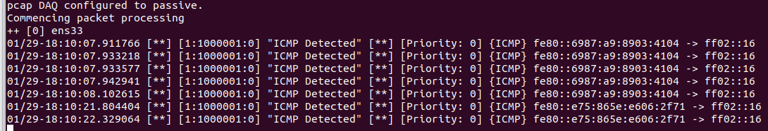
Step 15. Testing Snort with new rules!
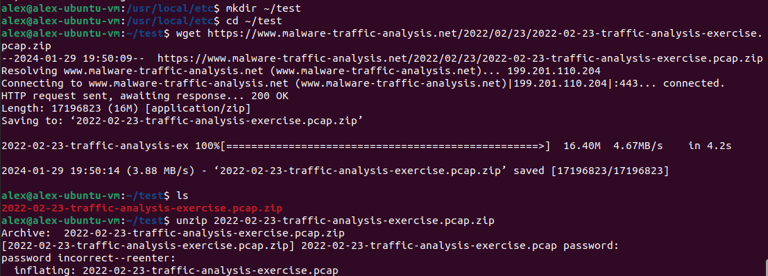
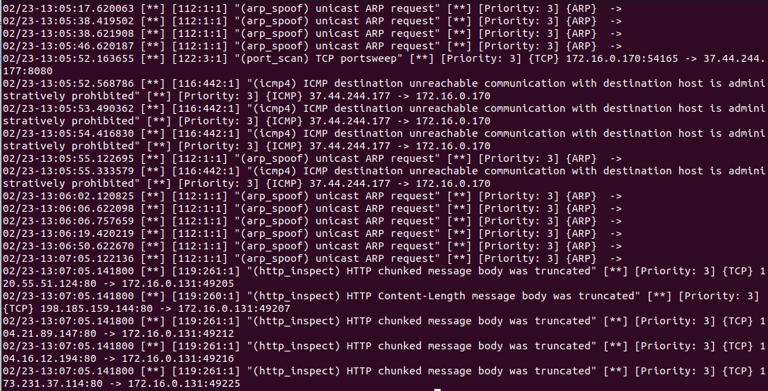
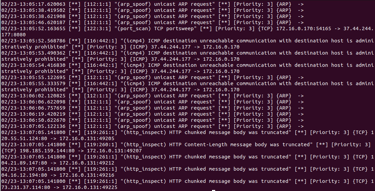
Creating a signature using Snort by downloading & analyzing a PCAP from Malware Traffic Analysis . net
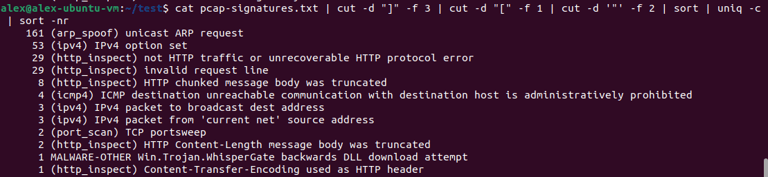
Very messy, cleaned up analysis using the "cut" and "sort" command. REGEX.
Malicious traffic has been discovered to the PCAP file host that generated from 156.96.154.210.